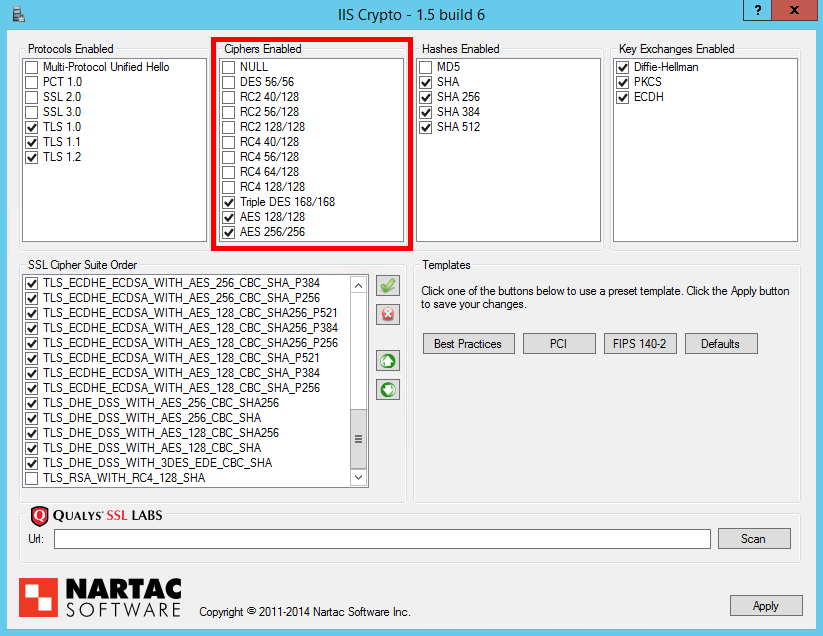
The OpenSSL EC library provides support for Elliptic Curve Cryptography (ECC). It is the basis for the OpenSSL implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA) and Elliptic Curve DiffieHellman (ECDH). Standards for Efficient Cryptography SEC 1: Elliptic Curve Cryptography Certicom Research Contact: Daniel R. Brown May 21, 2009 Elliptic curve cryptography is critical to the adoption of strong cryptography as we migrate to higher security strengths. NIST has standardized elliptic curve cryptography for digital signature algorithms in FIPS 186 and for key establishment schemes in SP A. The constant back and forth between hackers and security researchers, coupled with advancements in cheap computational power, results in the need for continued evaluation of acceptable encryption algorithms and standards. RSA is currently the industry standard for publickey cryptography and is used. Elliptical curve cryptography (ECC) is a public key encryption technique based on elliptic curve theory that can be used to create faster, smaller, and more efficient cryptographic keys. Security Builder Crypto supports the following elliptic curve algorithms: . ECDH and ECMQV ECC analogs of the DH and MQV key agreement algorithms, respectively. ; ECDSA An ECC analog of the DSA signature scheme for digital signature generation and verification. ; ECIES The Elliptic Curve Integrated Encryption Standard, also known as Elliptic Curve Encryption Scheme. If we're talking about an elliptic curve in F p, what we're talking about is a cloud of points which fulfill the curve equation. This equation is: This equation is: Here, y, x, a and b are all within F p, i. Elliptic Curve Public Key Cryptography The curve is intersected by lines in 0, 1, 2, or 3 places Touching in 1 place, a line is tangent to the curve Guide to Elliptic Curve Cryptography Springer New York Berlin Heidelberg Hong Kong London Milan Paris Tokyo Buy products related to elliptic curve cryptography products and see what customers say about elliptic curve cryptography products on Amazon. com FREE DELIVERY possible on eligible purchases Elliptic Curve Cryptography, or ECC, is a powerful, alternative approach to cryptography which can offer the same level of security at a much smaller size. Unter Elliptic Curve Cryptography (ECC) oder deutsch versteht man asymmetrische Kryptosysteme, die Operationen auf elliptischen Kurven ber endlichen Krpern verwenden. Diese Verfahren sind nur sicher, wenn diskrete Logarithmen in der Gruppe der Punkte der elliptischen Kurve nicht effizient berechnet werden knnen. Jedes Verfahren, das auf dem diskreten. In the second article of our Blockchain 101 series, Jimmy Song discusses elliptic curve cryptography (ECC). Why Is the NSA Moving Away from Elliptic Curve Cryptography? In August, I wrote about the NSA's plans to move to quantumresistant algorithms for its own cryptographic needs. Cryptographers Neal Koblitz and Alfred Menezes just published a long paper speculating as to the government's real motives for doing this. They range from some new cryptanalysis of ECC to a political need after the DUAL. We said that an elliptic curve defined over a finite field has a finite number of points. An important question that we need to answer is: how many points are there exactly? Firstly, let's say that the number of points in a group is called the order of the group. This ellipticcurve offers 128bit security and was designed to use with ellipticcurve DiffieHellman (ECDH) key exchange protocol. Curve has been adopted by popular messaging apps such as. Elliptic Curve Public Key cryptography started in the mid 1980's and a great deal of research has shown it is highly secure and efficient. Elliptic curve public key crypto systems have a lot of advantages compared with other public key methods. Lecture 14: Elliptic Curve Cryptography and Digital Rights Management Lecture Notes on Computer and Network Security by Avi Kak (kak@purdue. edu) Those of you who know what publickey cryptography is may have already heard of ECC, ECDH or ECDSA. The first is an acronym for Elliptic Curve Cryptography, the others are names for algorithms based on it. Today, we can find elliptic curves cryptosystems in. Elliptic Curve Cryptography: ECC (ECDLP). ECDSA (Elliptic Curve Digital Signature Algorithm) which is based on DSA, a part of Elliptic Curve Cryptography, which is just a mathematical equation on its own. ECDSA is the algorithm, that makes Elliptic Curve Cryptography useful for security. Elliptic Curve Cryptography has a reputation for being complex and highly technical. This isn't surprising when the Wikipedia article introduces an elliptic curve as a smooth, projective algebraic curve of. This is going to be a basic introduction to elliptic curve cryptography. I will assume most of my audience is here to gain an understanding of why ECC is an effective cryptographic tool and the Elliptic curve cryptography (ECC) is one of the most powerful but least understood types of cryptography in wide use today. An increasing number of websites make extensive use of ECC to secure. This is the primary motivation for SafeCurves. The SafeCurves criteria are designed to ensure ECC security, not just ECDLP security. SafeCurves: choosing safe curves for ellipticcurve cryptography. Elliptic curve cryptography is a branch of mathematics that deals with curves or functions that take the format Elliptic Curve Cryptography (ECC) was discovered in 1985 by Victor Miller (IBM) and Neil Koblitz (University of Washington) as an alternative mechanism for implementing publickey cryptography. Elliptic curve cryptography (ECC) is a public key cryptography method, which evolved form Diffie Hellman. To understanding how ECC works, lets start by understanding how Diffie Hellman works. The Diffie Hellman key exchange protocol, and the Digital Signature Algorithm (DSA) which is based on it, is an asymmetric cryptographic systems in. Elliptic curve cryptography is the most advanced cryptosystem in the modern cryptography world. It lies behind the most of encryption, key exchange and digital signature applications today. In mathematics, an elliptic curve is a plane algebraic curve defined by an equation of the form which is nonsingular; that is, the curve has no cusps or selfintersections. (When the coefficient field has Guide to Elliptic Curve Cryptography. Applications to Cryptography University of Wyoming June 19 July 7, 2006 0. An Introduction to the Theory of Elliptic Curves Outline Elliptic Curves What is an Elliptic Curve. An Elliptic Curve Cryptography (ECC) Tutorial Elliptic curves are useful far beyond the fact that they shed a huge amount of light on the congruent number problem. Elliptic Curve Cryptography in Practice Joppe W. Alex Halderman2, Nadia Heninger3, Jonathan Moore, Michael Naehrig1, and Eric Wustrow2 1 Microsoft Research 2 University of Michigan 3 University of Pennsylvania Abstract. Guide to Elliptic Curve Cryptography (Springer Professional Computing) [Darrel Hankerson, Alfred J. Menezes, Scott Vanstone on Amazon. FREE shipping on qualifying offers. After two decades of research and development, elliptic curve cryptography now. Elliptic curve cryptography, just as RSA cryptography, is an example of public key cryptography. The basic idea behind this is that of a padlock. If I want to send you a secret message I can ask you to send me an open padlock to which only you have the key. Elliptic Curve Cryptography (ECC) is one of the most powerful but least understood types of cryptography in wide use today. At CloudFlare, we make extensive use of ECC to secure everything from our customers' HTTPS connections to how we pass data between our data centers. MSR ECCLib is an efficient cryptography library that provides functions for computing essential elliptic curve operations on a new set of highsecurity curves. All computations on secret data exhibit regular, constanttime execution, providing protection against timing and cache attacks. ECC cryptography for secure devices software from Certicom addresses wireless security, anticloning, VoIP, ECC Tutorial. 4 Quiz 1 Elliptic curve groups over real numbers. To do elliptic curve cryptography properly, rather than adding two arbitrary points together, we specify a base point on the curve and only add that point to itself. For example, lets say we have the following curve with base point P. Elliptic Curve Cryptography can offer the same level of cryptographic strength at much smaller key sizes offering improved security with reduced computational requirements. Elliptic curve cryptography, in essence, entails using the group of points on an elliptic curve as the underlying number system for public key cryptography. There are two main reasons for using If you want to know how to encrypt data using Elliptic Curve Algorithm in C# , then this tip is for you. Answer: ECC is an asymmetric cryptography algorithm which involves some high level calculation using mathematical curves to encrypt and decrypt data. It is similar to RSA as it's asymmetric but it. Elliptic Curve Cryptography in Practice Joppe W. Alex Halderman2, Nadia Heninger3, Jonathan Moore, Michael Naehrig1, and Eric Wustrow2 1 Microsoft Research 2 University of Michigan 3 University of Pennsylvania Abstract. In this paper, we perform a review of elliptic curve cryptography (ECC), as it is John Wagnon discusses the basics and benefits of Elliptic Curve Cryptography (ECC) in this episode of Lightboard Lessons. Check out this article on DevCentra A short video I put together that describes the basics of the Elliptic Curve DiffieHellman protocol for key exchanges. Elliptic Curve Cryptography Tutorial. Elliptic Curve Cryptography, or ECC, is the kind of cryptography most widely used for blockchains. It is used to validate new transactions to the blockchain and. For many operations elliptic curves are also significantly faster; elliptic curve diffiehellman is faster than diffiehellman. Note Curves with a size of less than 224 bits should not be used..